Sometimes it happens, that FortiOS is not updating it’s antivirus signatures anymore. The monitoring software, a monitoring script or a very attentive administrator is then reporting this problem to the FortiGate admin to fix it. This guide will lead you through the steps to troubleshoot this.
How to check signature versions on your FortiGate
With the CLI command “diagnose autoupdate versions” you can show the versions of the currently installed databases.
fortigate01 # diagnose autoupdate versions AV Engine --------- Version: 6.00270 Contract Expiry Date: Mon Jan 1 2023 Last Updated using scheduled update [long time ago] Last Update Attempt: Fri Mar 9 12:34:56 2022 Result: No Updates Virus Definitions --------- Version: 90.01112 Contract Expiry Date: Mon Jan 1 2023 Last Updated using scheduled update [long time ago] Last Update Attempt: n/a Result: Updates Installed Extended set --------- Version: 90.01112 Contract Expiry Date: Mon Jan 1 2023 Last Updated using scheduled update [long time ago] Last Update Attempt: Fri Mar 9 12:34:56 2022 Result: Connectivity failure Mobile Malware Definitions --------- Version: 90.00154 Contract Expiry Date: Mon Jan 1 2023 Last Updated using scheduled update [long time ago] Last Update Attempt: Fri Mar 9 12:34:56 2022 Result: Updates Installed
How to check the latest signature versions on www.fortiguard.com
Open the website www.fortiguard.com, scroll to the bottom (to “Service Updates”) and compare the version shown on the CLI output with the latest version number published on the FortiGuard website.
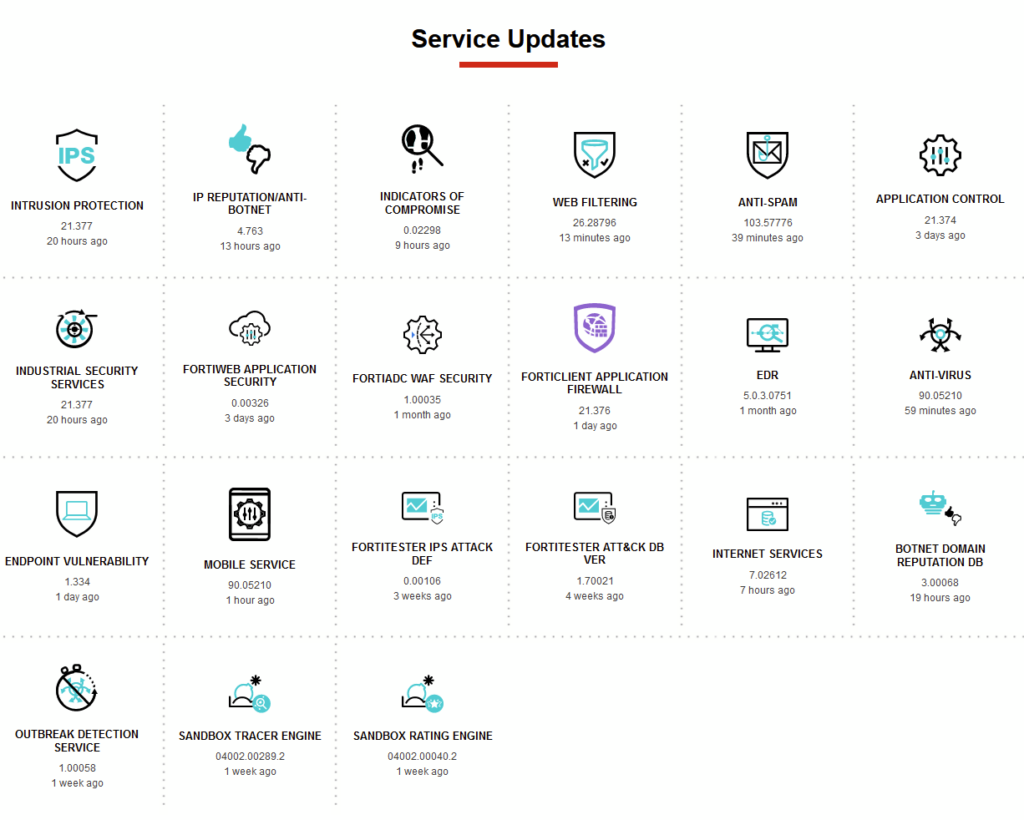
Version numbers are aligned
If the version shown on the FortiGate is aligned with the latest version shown on the FortiGuard website, everything is fine and nothing needs to be done.
Version numbers are different
If the version shown on the FortiGuard website is newer than the currently installed version, you need to check if the contract for the package is already expired. To check this, just compare the “Contract Expiry Date” with the current date.
If the contract is still valid, you may try to execute “execute update-now” to manually initiate an update cycle on the FortiGate. Please note, that the update may take up to 5 Minutes on your FortiGate and that no status update is shown during the update process if you have not enabled the process debugging by using the commands below:
diagnose debug enable diagnose debug application update -1 execute update-now
Version numbers are still different
If the CLI command “execute update-now” and the five minute coffee-break did not solve the issue, you may want to check if somewhere an antivirus profile (/ips profile/dnsfilter profile/…) is being applied on a firewall policy.
As soon as the service, like AV, is not enabled in a firewall policy anymore, the FortiGate will stop updating the database for the service. As soon as the service is being applied in a firewall policy again, the database will also get updated again.
As soon as the service, like AV, is not enabled in a firewall policy anymore, the FortiGate will stop updating the database for the service.
If you use the default antivirus database and the extended set is not enabled, the extended set database will not get updated because it is not necessary.
Problem still not solved?
There are three different support articles regarding FortiGuard update issues which can be found under https://docs.fortinet.com/document/fortigate/6.2.10/cookbook/127191/fortiguard-troubleshootinghttps://docs.fortinet.com/document/fortigate/6.2.10/cookbook/127191/fortiguard-troubleshooting
![]()

