Traffic can be UTM inspected on the FortiGate either flow-based or proxy-based. Both inspection modes have advantages and disadvantages. Therefore it is very important to use the right inspection mode for the concerning purpose.
Flow based inspection
- Default inspection mode
- Uses single-pass direct filter approach (DFA) pattern matching to identify possible attacks or threats
- File is scanned on a flow basis as it passes through FortiGate
- Requires fewer processing resources
- Provides faster scanning
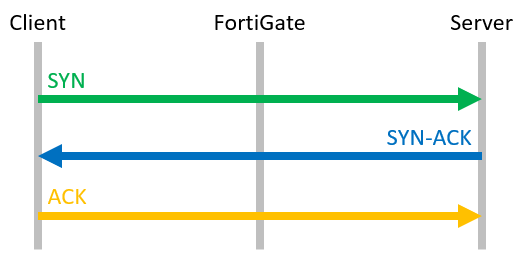
If you sniff a flow based session, you can see this behaviour:
FGT # diag sniffer packet any 'host 203.0.113.28' 4 interfaces=[any] filters=[host 203.0.113.28] # The FortiGate receives the SYN packet from the client ... 0.000000 lan in 192.168.1.22.21137 -> 203.0.113.28.80: syn 1706835036 # ... and sends the packet directly further to the Webserver. 0.000051 wan out 11.22.33.44.21137 -> 203.0.113.28.80: syn 1706835036 # The webserver sends it's SYN/ACK packet which is also directly forwarded to the Client. 0.007561 wan in 203.0.113.28.80 -> 11.22.33.44.21137: syn 187701112 ack 1706835037 0.007577 lan out 203.0.113.28.80 -> 192.168.1.22.21137: syn 187701112 ack 1706835037 # The last packet of the TCP handshake is the ACK packet, which is also forwarded to the Webserver immediately. 0.008548 lan in 192.168.1.22.21137 -> 203.0.113.28.80: ack 187701113 0.008566 wan out 11.22.33.44.21137 -> 203.0.113.28.80: ack 187701113
Proxy based inspection
- More thorough inspection
- Adds latency
- Complete content is scanned
- Two TCP connections (From client to FortiGate acting as proxy server / From FortiGate to server)
- Communication is terminated on Layer 4
- More resource intensive
- Provides a higher level of threat protection
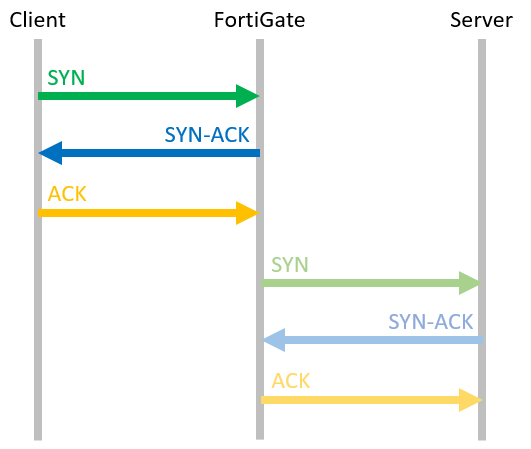
If you sniff a flow based session, you can see this behaviour:
FGT # diag sniffer packet any 'host 203.0.113.28' 4 interfaces=[any] filters=[host 203.0.113.28] # The FortiGate receives the SYN packet from the client ... 0.000000 lan in 192.168.1.22.21213 -> 203.0.113.28.80: syn 2610810331 # ... and answers directly with a SYN/ACK packet to establish the session between Client and FortiGate. 0.000049 lan out 203.0.113.28.80 -> 192.168.1.22.21213: syn 3433523664 ack 2610810332 # As soon as the FortiGate receives the ACK packet from the client, ... 0.000131 lan in 192.168.1.22.21213 -> 203.0.113.28.80: ack 3433523665 # ... the FortiGate contacts the Webserver by sending a SYN packet to establish the TCP connection. 0.001407 wan out 11.22.33.44.21213 -> 203.0.113.28.80: syn 2081136307 # While the FortiGate waits for the first answer (SYN/ACK packet) from the server, it already receives traffic of this session from the Client. 0.001713 lan in 192.168.1.22.21213 -> 203.0.113.28.80: psh 2610810332 ack 3433523665 0.001722 lan out 203.0.113.28.80 -> 192.168.1.22.21213: ack 2610810933 # Underneath, the FortiGate finished the handshake with the Webserver and establishes the connection between FortiGate and Webserver. 0.009107 wan in 203.0.113.28.80 -> 11.22.33.44.21213: syn 266185062 ack 2081136308 0.009123 wan out 11.22.33.44.21213 -> 203.0.113.28.80: ack 266185063
Traffic, matching policies that do not use Flow- or Proxy based inspection or no UTM inspection at all
… are handled from the FortiOS kernel and the process is called “stateful inspection”. Since the traffic is not sent to the IPS Engine (for flow based inspection) or the WAD daemon (for proxy based inspection), this mode uses fewer system ressources.
Which inspection mode to choose
Flow-based inspection takes a snapshot of content packets and uses pattern matching to identify security threats in the content.
Flow inspection is recommended for policies that prioritize traffic throughput, such as allowing connections to a streaming or file server.
Proxy-based inspection reconstructs content passing through the FortiGate and inspects the content for security threats.
Because proxy mode provides the most thorough inspection, it is recommended that you use proxy inspection for policies where preventing data leakage or malicious content is critical.
Each inspection mode plays a role in processing traffic as it travels to its destination. While both modes provide significant security, proxy-based provides more feature configuration options, while flow-based is designed to optimize performance.
Information Sources
The content of this article is derived from several Fortinet information sources linked below:
https://docs.fortinet.com/document/fortigate/7.4.1/administration-guide/721410/inspection-modes
FortiGate Administrator (FCP) and Fortinet Enterprise Firewall (FCSS) courseware.
![]()

