If you want to configure rules for Saas services on the PaloAlto Firewall, you can do this using the App ID for the particular service, or you can use the IP addresses, Domains or URLs of the service in the policy.
However, since Saas services typically do not use only one IP address, domain or URL, and since these can change dynamically, it requires a dynamic list that is constantly updated automatically.
PaloAlto offers this service as “EDL hosting service”. External Dynamic Lists (EDL) are dynamic lists that can contain a list of IP addresses, domains or URLs. These lists are periodically queried by the firewall and updated accordingly. These EDL lists can then be used in various policies. Due to the automatic update of the lists, they are always up to date. There is also no need to commit the configuration if the list changes.
PaloAlto offers a large number of lists with this hosting service. These are partially divided by country and by the specific Saas services.
EDL Hosting Service
https://docs.paloaltonetworks.com/resources/edl-hosting-service.html
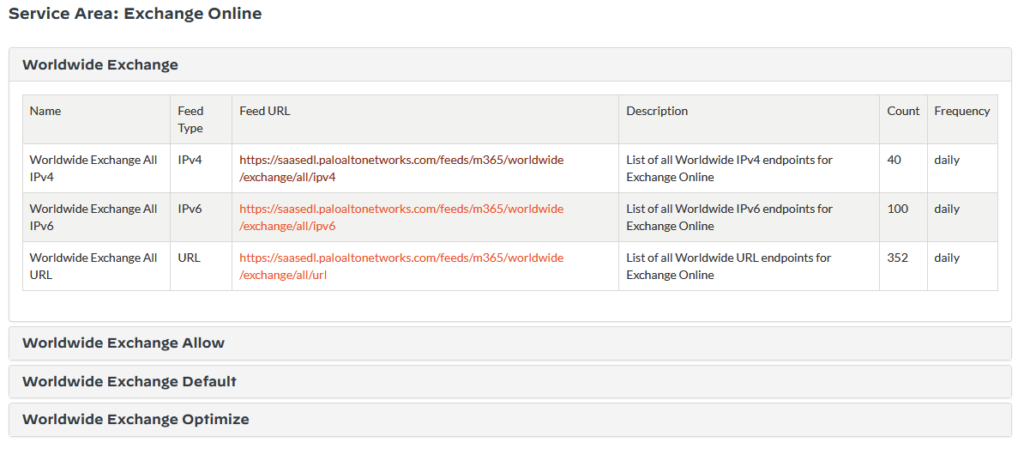
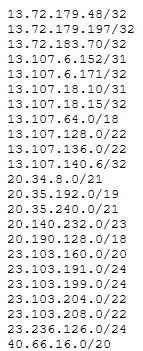
To view the content of a list, click on the link and you will get the list of IP addresses, domains or URLs. Here an example of an IP list:
To use the list, it must be configured as an EDL list. Because the list is provided as encrypted connection via HTTPS, the root certificate must be imported and selected in the EDL list. Therefor you need to upload the root certificate first, create a certificate profile and use it in the EDL configuration.
The root certificate in pem format can be found here.
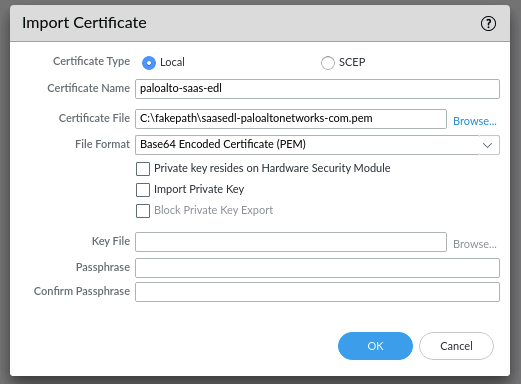
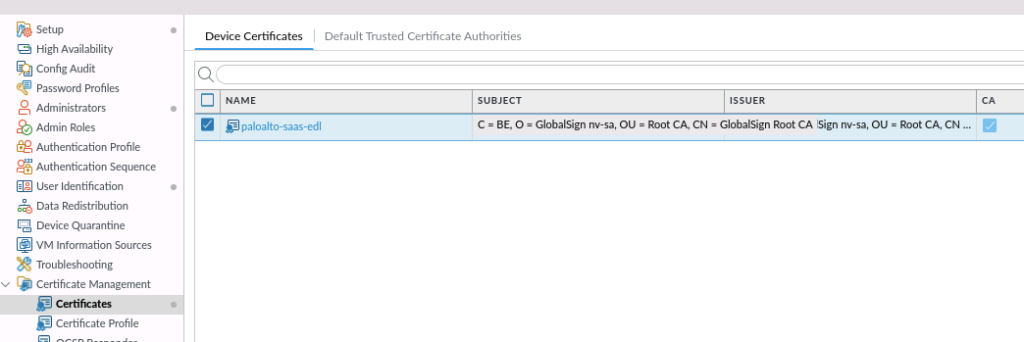
Then create a certificate profile and choose the uploaded certificate in the profile:
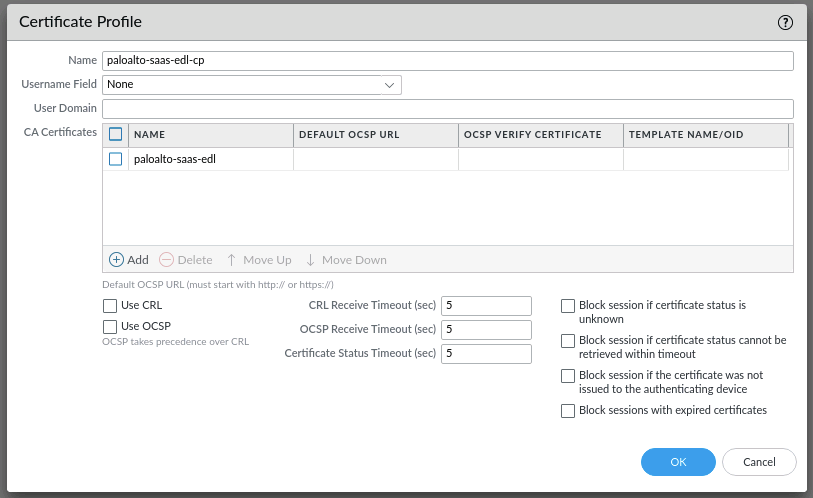
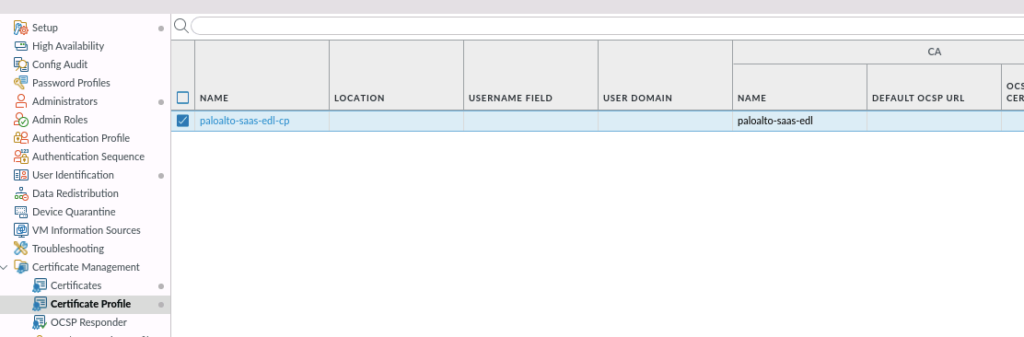
Configure now the EDL list and choose the certificate profile:
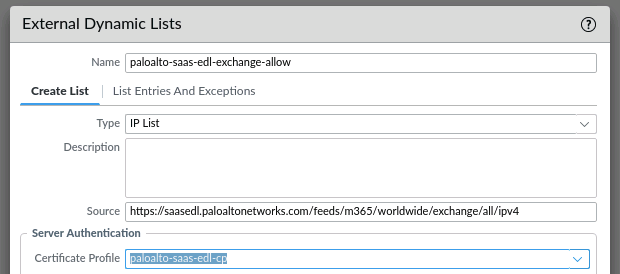
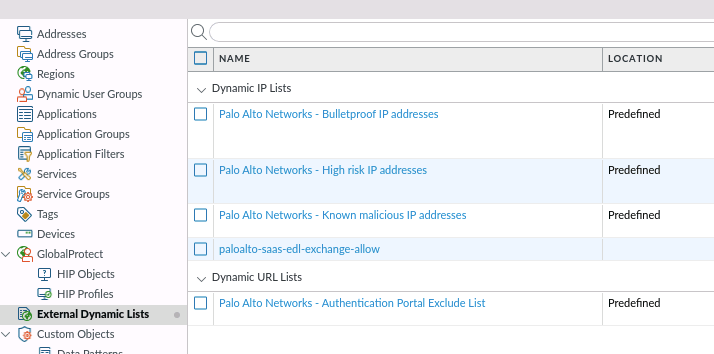
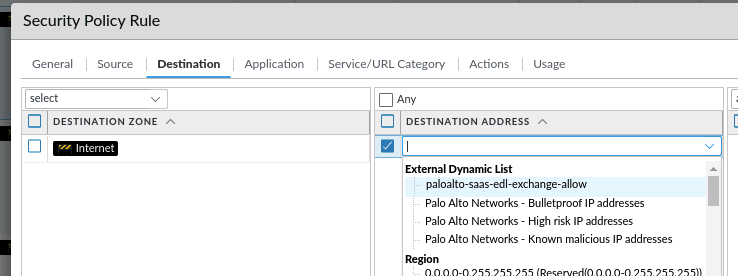
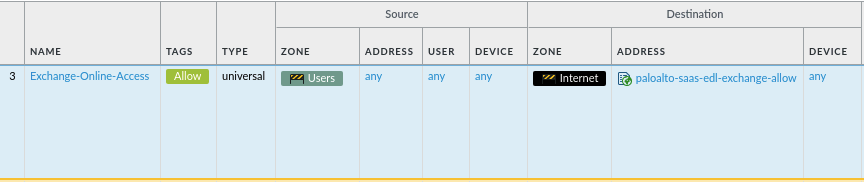
Now you can use the EDL in your policy rule set. Here an example of the security policy rule:
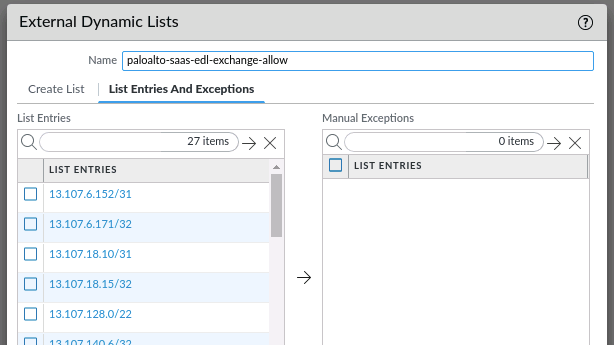
Commit and verify if the list can download the entries:
![]()

