The number of ransomware incidents has exploded in the last few years, infecting hundreds of thousands of systems worldwide. Ransomware is malware that’s designed to hold your data hostage unless you pay up. Wait too long —or try to rescue it — and that data can be gone for good.
To protect your network and computers from ransomware and other malicious malware, be sure to first perform these fundamental tasks:
- Backup and recovery
- Segment BYOD (Bring Your Own Devices) from main network
- Run antivirus software on clients
Is Your Firebox Ready to Block Ransomware?
Follow these steps to defend your network from malicious malware.
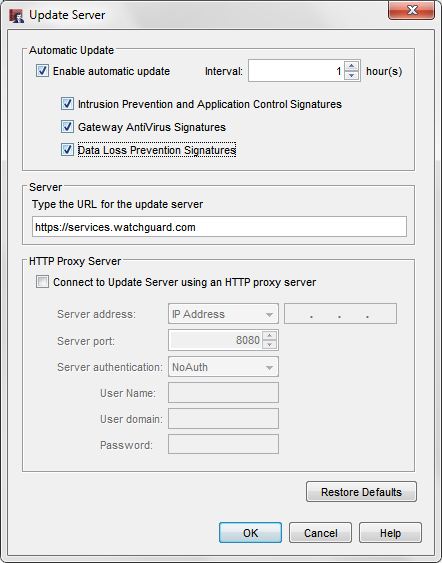
Signature Updates
- Make sure the signatures for Gateway AntiVirus, IPS, and Application Control are up to date.
- Enable automatic updates of all your signatures.
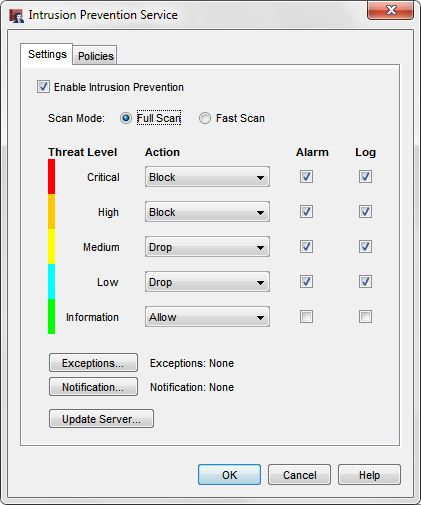
Intrusion Prevention (IPS)
- Enable IPS on all outbound policies, especially the default “Outgoing” policy.
- Make sure your IPS signatures are up to date. IPS signatures are always changing to keep up with new threats, and you can enable automatic signature updates so that you always have the latest version of signatures. You can search and view the current WatchGuard threat database at http://www.watchguard.com/SecurityPortal/ThreatDB.aspx.
- In some high security environments you may want to use a more aggressive action for “Critical” and “High” threat levels, and set them to “Block”. The “Block” action will add the source of the IPS intrusion to the Blocked Sites List for 20 minutes.
- Select the Alarm and Log options for each threat level so that you receive email notifications in the event a malware threat is detected.
There are 2 different scan modes you can choose from “Full Scan” or “Fast Scan”.
- Full Scan — Scan all packets for policies that have IPS enabled.
- Fast Scan — Scan fewer packets to improve performance. This option greatly improves the throughput for scanned traffic, but does not provide the comprehensive coverage of Full Scan mode. This is the default setting.
Beginning in Fireware OS v11.8, “Fast Scan” is the default scan mode for IPS. In environments with high value data, you can switch to “Full Scan”. Performance will be affected when you use the “Full Scan” option.
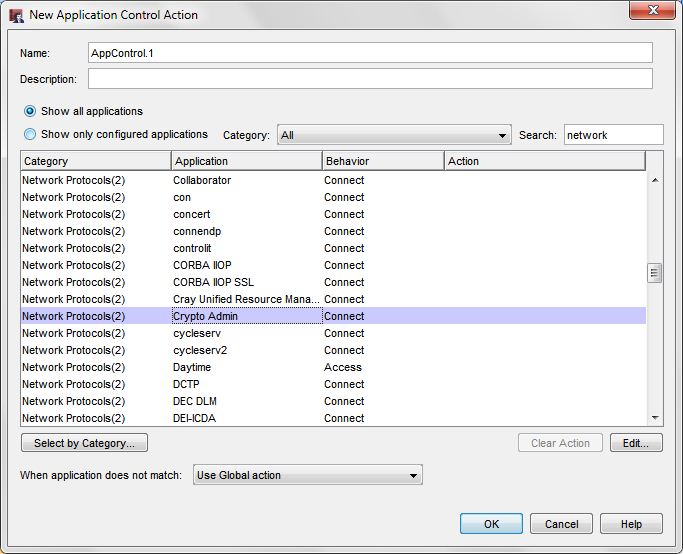
Application Control
- Enable Application Control on all outgoing policies including the default “Outgoing” policy.
- Application Control has a “Crypto Admin” application as part of the Network Protocols category to detect CryptoWall, CryptoLocker, and their variants. Make sure the action for this application is set to “Drop”.
- We recommend that you also block access to these applications that can spread malicious malware:
- BitComet
- BitLord
- BitTorrent Series
- aMule
- easyMule
- eMule
- eMule Plus
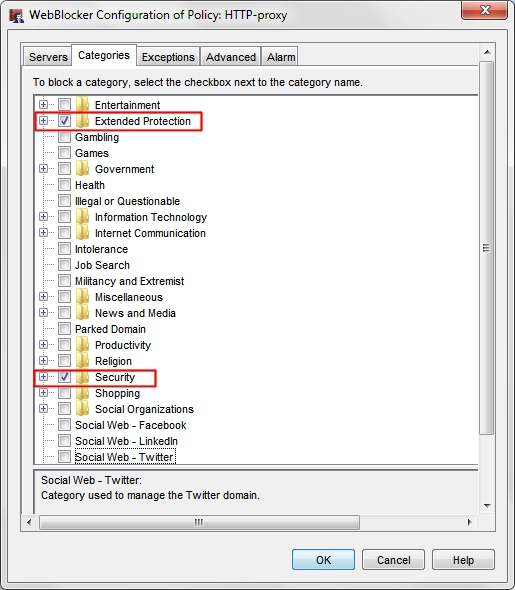
WebBlocker
- Enable WebBlocker on your HTTP and HTTPS proxy policies to protect your web traffic.
- Use the Websense cloud service that contains 130 security categories.
- Make sure these two Websense categories are selected to block access to malware sites:
- Security
- Extended Protection
Gateway AntiVirus
- Enable Gateway AntiVirus on your HTTP, FTP, SMTP, POP3, TCP-UDP proxy policies.
- Make sure your Gateway AntiVirus signatures are up to date. Enable automatic signature updates so that you always have the latest version of signatures.
- In the global Gateway AntiVirus settings, select the Enable Decompression option to scan inside compressed files such as .zip archives.
- In the HTTP Response > Content Types proxy action settings for Gateway AntiVirus, make sure you set the action to AV Scan for “pdf”, “javascript” and “shockwave-flash” content types.
- In the HTTP Response > Body Content Types proxy action settings for Gateway AntiVirus, make sure you set the action to Deny or AV Scan for .exe files.
- For each proxy, we recommend you add similar file types that can contain malware such as scripts, Windows system files, and office application macros.
Note: Smaller WatchGuard devices with less memory resources use a subset of the Gateway AntiVirus signatures. In high risk environments, we recommend you deploy Firebox devices with more resources to get the larger signature set.

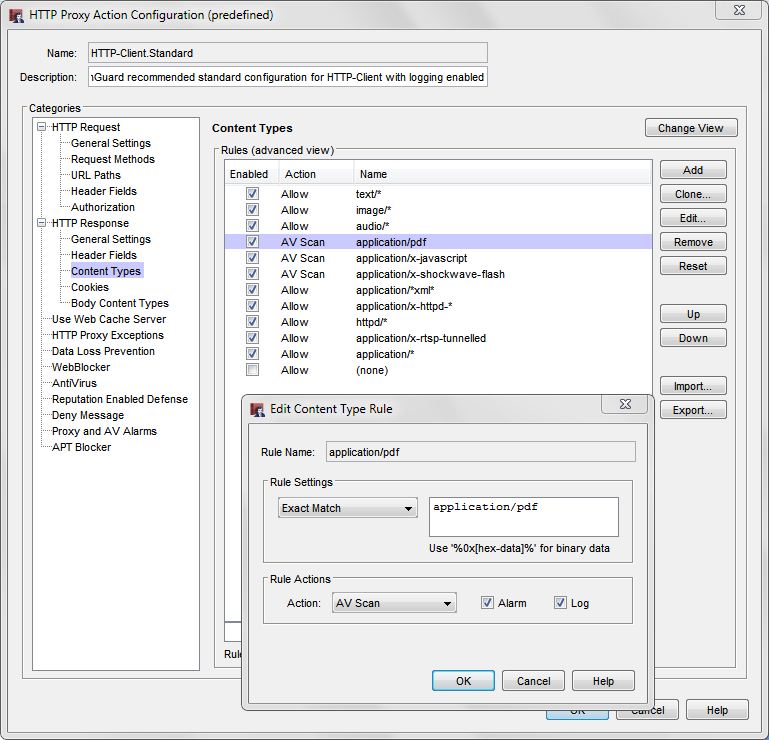
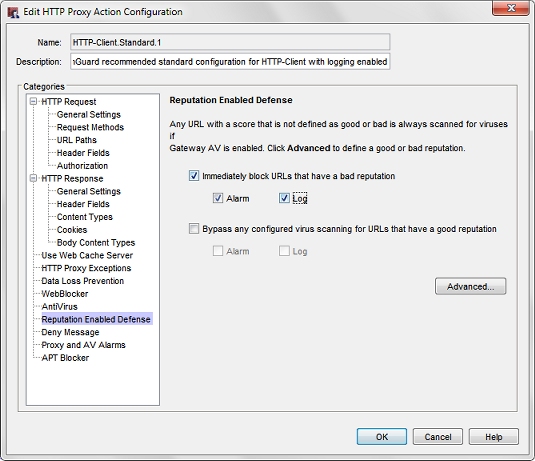
Reputation Enabled Defense
Use Reputation Enabled Defense on your HTTP-proxy policies to block access to URLs with poor reputations.
In the Reputation Enabled Defense configuration, enable this option:
- Immediately block URLs that have a bad reputation
Enable the Alarm and Log options for notifications and for logging and reports.
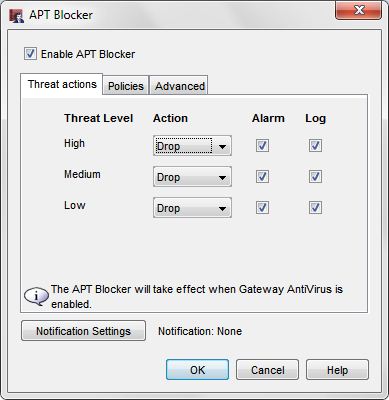
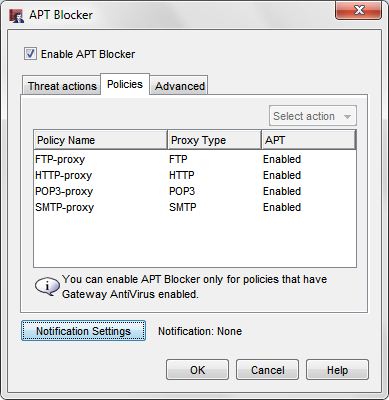
APT Blocker
APT Blocker uses cloud-based scanning of files to detect zero-day malware. The APT Blocker subscription service is an add-on subscription service and is not included in the standard security subscription suite on your Firebox.
- Enable APT Blocker on your HTTP, FTP, SMTP, and POP3 proxy policies.
- Enable the Alarm and Log options to immediately notify you by email when APT malware is detected and log the event for reports.
spamBlocker
Enable spamBlocker on your SMTP and POP3 proxies.
Dimension
Quellenangabe: www.watchguard.com, Knowledge Base Artikel 000008694
Diese Angaben sind auch als PDF verfügbar: How to prevent ransomware


Thanks for the information, very well done.