We have recently seen an accumulation of problems with IPSec VPN tunnels.
The problem was recognized by Swisscom and fixed with a new firmware. Further information can be found in the release notes (on this page). The firmware version from which the problem was fixed is: 9.52.12 B16++ (June 2023).

The following symptoms are very typical to identify this problem
- The IPSEC Tunnel is up, but no or only one-way traffic flow is going through the tunnel.
- If there are multiple VPN tunnels set up, only one or a few of all the tunnels may be affected.
- The problem is highly sporadic.
- The problem is not related to a firewall vendor.
- Internet line is provides by Swisscom with a Business DSL modem. Known as Smart BCON or SBCON.
- Also, modems from Fritzbox! and UPC or Sunrise were affected in some cases.
How to check if you are affected by this issue
For a first overview, you can check the Outgoing and Incoming Data counter on the Firewall. You can see there, that one of the counters is not incrementing anymore:
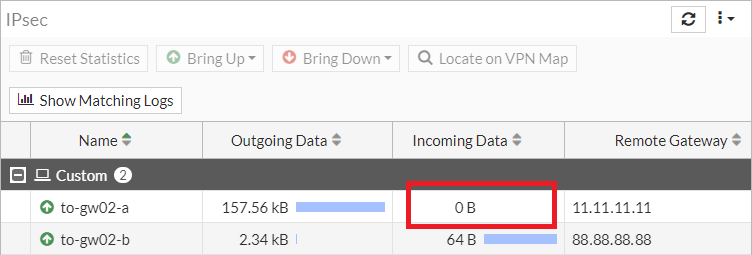
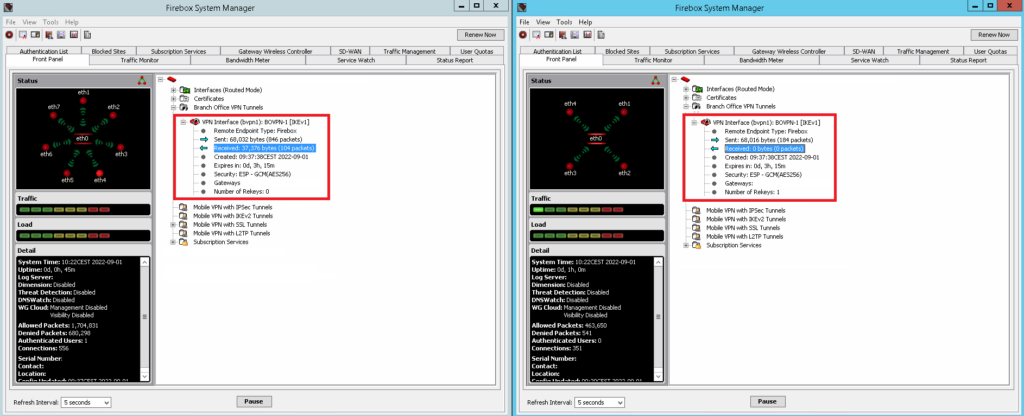
For a more reliable troubleshooting, you can do a packet trace on both sides of the VPN tunnel. You should see incoming and outgoing ESP packets. If you only see outgoing but no incoming ESP packets, you are probably affected by this issue.
FortiGate CLI command
1.2.3.4 should be replaced by the remote public IP terminating the VPN tunnel.
# Temporarily disable the hardware acceleration
# Please note disabling NP will cause the tunnel to flap
config vpn ipsec phase1-interface
edit phase-1-name
set npu-offload disable
end
# Capture the ESP packets
diagnose sniffer packet any "host 1.2.3.4 and esp" 4 0 a
# Turn the hardware acceleration back on
config vpn ipsec phase1-interface
edit phase-1-name
unset npu-offload
endWatchGuard Diagnostic Task > TCP Dump
Replace 1.2.3.4 by the remote public IP terminating the VPN tunnel.
Enable Advanced Options > -i any host 1.2.3.4 and espTemporary solution
- Reboot the firewall
- Reboot the router
- Enforce or enable NAT-Traversal
How to disable the IPSec feature on a Swisscom router
We found out that this issue could be related to the enabled Peer-to-Peer VPN function on the Swisscom router.
You can disable the function for test purposes as follow:
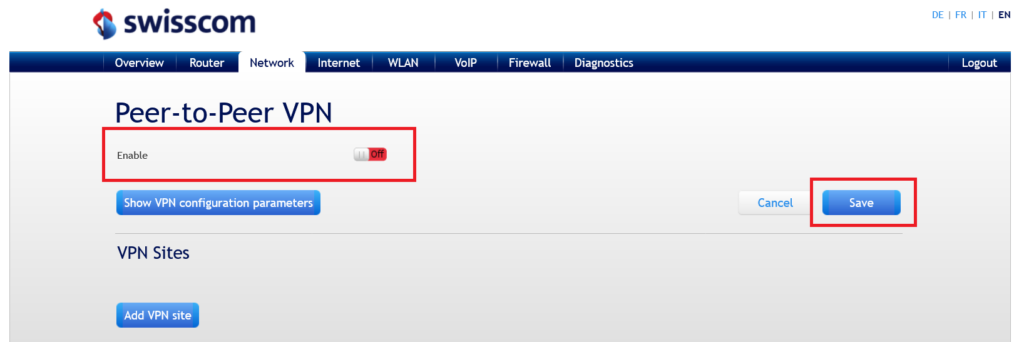
As soon as the function is disabled and the router is rebooted, the problem is resolved.
Please note, that the solution (disabling the VPN feature) has to be implemented on both sides of the tunnel. Also, the VPN feature could be enabled again after a firmware upgrade on Swisscom routers.
Please note, that it also may possible that other router models are affected by this issue and we are just not yet aware of it. Please let us knowin the comments if you experience similar issues with your setup.
If the problem is still not solved after disabling the VPN feature on your router, you may have a look into our Blog Post Fortigate S2S-Dialup VPN – Traffic does not run through IPsec tunnel anymore.
![]()


Guten Tag,
wir hatten das Problem auch mit verschiedenen Zyxel Modellen in den letzten Monaten. Heute habe ich gehört, dass Swisscom jetzt an einer neuen Firmware arbeiten soll, die das Problem behebt.
In keinem der Fälle die ich gesehen habe war der IPsec Funktion im Centro Business aktiviert und trotzdem trat das Problem auf. Ich beobachtete eher das Gegenteil, d.h. nachdem ich die IPsec Funktion einschaltete trat der Fehler nicht mehr auf, dies jedoch nur bei einer Firewall.
Beste Grüsse
Ueli Strasser
Guten Tag Herr Strasser
Besten Dank für Ihren Kommentar.
Wie im Beitrag erwähnt tritt das Problem unabhängig von der verwendeten Firewall oder VPN Lösung auf. Es ist daher naheliegend, dass es auch mit ZyXEL Firewalls auftritt.
Die IPSec Funktionalität ist auf den Swisscom Geräten wie im Beitrag genannt per Standardeinstellung aktiv. Uns sind zahlreiche Fälle bekannt, bei denen das Problem durch das deaktivieren der “Peer-to-Peer VPN” Funktion auf dem Router behoben werden konnte. Bisher ist Ihr Bericht aber der erste, dass das Problem erst durch das aktivieren der Funktion behoben wird.
Wir freuen uns aber trotzdem, dass unser Blog Ihnen zum finden der passenden Lösung eine Hilfe war.
Freundliche Grüsse und ein schönes Wochenende,
Das Boll Tech Team
Gemäss folgendem Swisscom-Post wurde der Fehler in der Firmware 9.52.12 gelöst.
Da mit der Firmware 9.52.10 in zunehmenden Fällen gemeldet wurde, dass es zu Verbindungsproblemen von VPN-Verbindungen kommt, wurde dieser Fehler nach intensiver Analyse umgehend korrigiert. Der automatische Rollout wird primär auf all die Geräte vorgesehen, welche fixe IP-Adressen verwenden.
Da die Firmware primär Fehlerbehebungen enthält, wird der automatische Rollout umgehend gestartet.
Router-Modell Centro Business 2.0
Firmware Ist / Soll 9.52.10 / 9.52.12
Auto. FW Update-Phase Ca. 15.06.2023 – 28.06.2023
Guten Tag Peter
Besten Dank für Deinen Kommentar und vielen Dank für den Hinweis.
Wir verlinken hier gerne noch auf die Release Notes in welchen die Infos zu finden sind. Die Release Notes selber sind auf der Swisscom Seite zu finden.
Damit hoffen wir, dass das Problem endgültig aus der Welt geschafft werden kann.
Freundliche Grüsse,
Das Boll Tech Team