
Quellenangabe:
Jonas Spieckermann, Watchguard
Artikel vom WatchGuard Security Center:
http://watchguardsecuritycenter.com/
Last week, a new ransomware variant called Locky began spreading in the wild.
Locky encrypts data on an infected system using AES encryption, and then leaves a blackmail letter (which is localized in several languages) asking for half a bitcoin to get your data back. More disturbingly, it also searches for any network share (not just mapped shares), and encrypts data on those remote shares as well. If you leverage cloud storage solutions, your backup may get infected as well when it synchronizes the encrypted files. Currently, researchers have not found a way to decrypt files Locky has locked.
Kevin Beaumont, one of the security researchers studying this ransomware, managed to intercept some of the domains Locky uses for its Command & Control (C&C) channel. This allowed him to estimate infection rates, and he found Locky seems to infect over 100,000 victims per day. Infection rates varied by country, lead by Germany with around 5000 new infections per hour at its peak.
In most cases, Locky arrives in an email that includes an Office document with a malicious macro. If you open the document, it tries to infect you with the ransomware. Other variants sometimes arrive as a .zip file, which contains some malicious Javascript. The emails are mainly fake invoices.
Last Thursday, I personally received a variant of Locky in an attachment called “Rechnung-263-0779.xls” (which is German for “invoice”) in a Spam inbox. I decided to use this file to analyze all the ways WatchGuard’s unified threat management (UTM) appliances could stop this brand new ransomware.
To start, I uploaded the infected file to www.virustotal.com to see which antivirus (AV) vendors had a signature available. As the email was already in my inbox for over 24 hours, 26 out of 55 AV scanners were able to detect it. AVG—the AV engine WatchGuard uses for Gateway AntiVirus (GAV)—was on that list. So right away, WatchGuard’s GAV service can block this particular variant from reaching our customers.
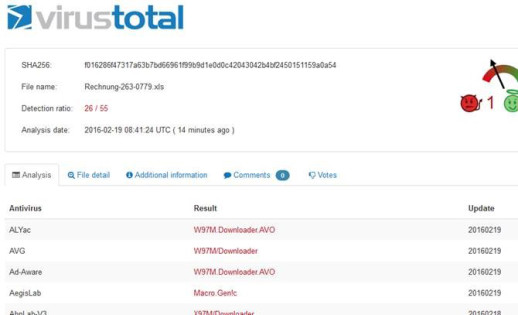
Nowadays, malware changes and evolves quickly, which is why signature-based AV often can’t keep up with the latest threats. To combat this problem, WatchGuard offers another layer of protection to detect brand new, never before seen malware files. We call this solution APT Blocker. I also ran this ransomware variant through our next-gen sandbox, to see whether or not APT Blocker detected the file’s bad behavior. It did! The malicious “invoice” file received a score of 99/100 which represents a high risk. It’s particularly important to understand the added benefit of the APT blocker solution. Even if the file used to deliver Locky changes, its behaviors won’t. That’s why this solution can catch new things signatures might miss.
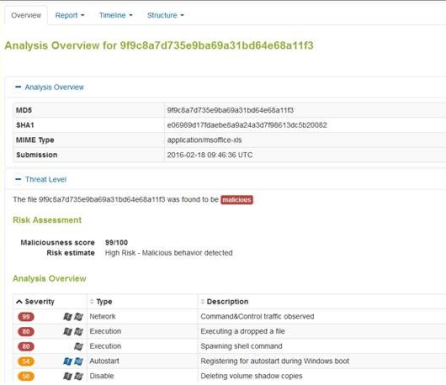
Figure 3: APT Blocker sandbox detects Locky
Another question came to my mind: What happens if the ransomware is already in place, or reaches the system from another source (e.g. USB drive)?
As I mentioned earlier, Kevin Beaumont managed to identify some of the domains Locky uses for its for C&C connections. WebBlocker, the URL categorization service in WatchGuard Fireware, treats them as subcategories of “Security” or “Extended Protection”. If you block these categories with WebBlocker, it prevents Locky from calling home, and also helps you identify systems that have gotten infected. To verify this, I entered one of Locky’s known C&C domains into our online tool to confirm that we indeed list it as a known bot network channel.
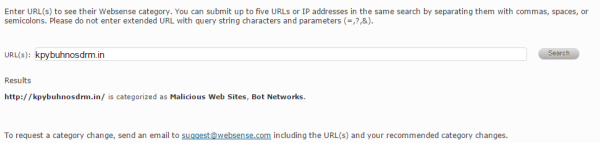
Figure 4: WatchGuard WebBlocker recognizes Locky domain as malicious
Once I verified that many of our UTM’s security services could detect Locky, I ran through one last test… I personally tried to download the malicious file “Rechnung-263-0779.xls” from my webmail.
I’ve configured my WatchGuard Firebox with HTTPS Deep Inspection. This feature allows WatchGuard’s security services, such as GAV and Intrusion Prevention Service (IPS), to run security scans even on encrypted web traffic, like the webmail I was using to download this ransomware. Despite the encrypted webmail connection, our Firebox detected and blocked the Locky invoice file with the GAV service. It was unable to reach my workstation.
As you can see, WatchGuard XTM and Firebox appliances have several features that can help prevent ransomware like Locky. However, these protections only work if you turn them on and configure them properly. If you want to keep Locky off your network , I highly recommend you read the Knowledgebase Article “How to prevent ransomware and other malicious malware with your Firebox”

