Palo Alto Networks discovered a vulnerability (CVE-2024-3400) with a CVSSv4.0 base score of 10 that impacts PAN-OS version 10.2+ with GlobalProtect enabled. We strongly recommend all to review the advisory for remediation steps.
Are you affected?
This vulnerability does not apply to you if any one of the following apply:
- You are running a PAN-OS version < 10.2
- You do not have GlobalProtect Gateway enabled
- You do not have telemetry enabled. Update 17.4.2024: Having telemetry enabled is not necessary for PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1 to be vulnerable. Please upgrade asap to the recommended hotfixes when using GlobalProtect.
Update 17.4.2024: The ASC Partner Auto Assistant tool has been updated with signatures to detect any IOCs for the devices that may have been compromised. If you want us to check if your device has been compromised, please contact us via our support channel.
Afftected PANOS versions
Please check if you are running one of the affected PANOS software versions.
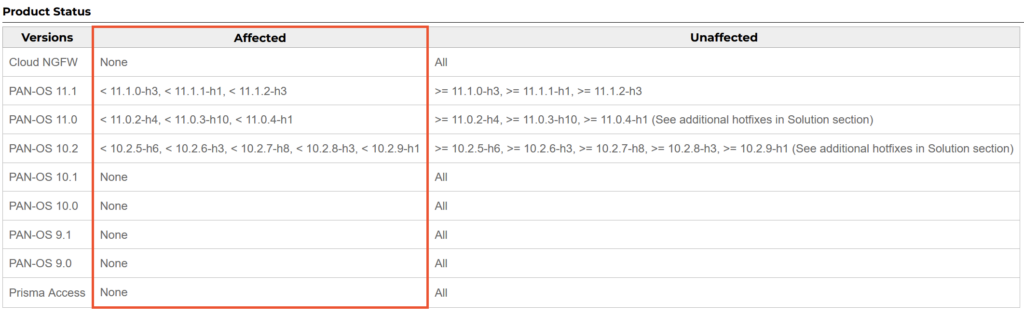
Update 17.4.2024: Updated list of patches and ETA
PAN-OS 10.2:
- 10.2.9-h1 (Released 4/14/24)
- 10.2.8-h3 (Released 4/15/24)
- 10.2.7-h8 (Released 4/15/24)
- 10.2.6-h3 (Released 4/16/24)
- 10.2.5-h6 (Released 4/16/24)
- 10.2.3-h13 (ETA: 4/17/24)
- 10.2.1-h2 (ETA: 4/17/24)
- 10.2.2-h5 (ETA: 4/18/24)
- 10.2.0-h3 (ETA: 4/18/24)
- 10.2.4-h16 (ETA: 4/19/24)
PAN-OS 11.0:
- 11.0.4-h1 (Released 4/14/24)
- 11.0.3-h10 (Released 4/16/24)
- 11.0.2-h4 (Released 4/16/24)
- 11.0.1-h4 (ETA: 4/17/24)
- 11.0.0-h3 (ETA: 4/18/24)
PAN-OS 11.1:
- 11.1.2-h3 (Released 4/14/24)
- 11.1.1-h1 (Released 4/16/24)
- 11.1.0-h3 (Released 4/16/24)
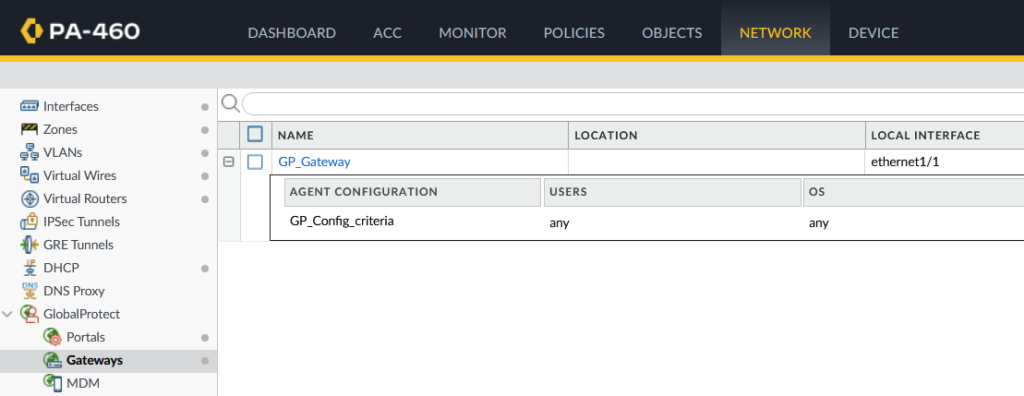
GlobalProtect configuration
You can verify whether you have a GlobalProtect Gateway configured by checking for entries in your firewall web interface (Network > GlobalProtect > Gateways).
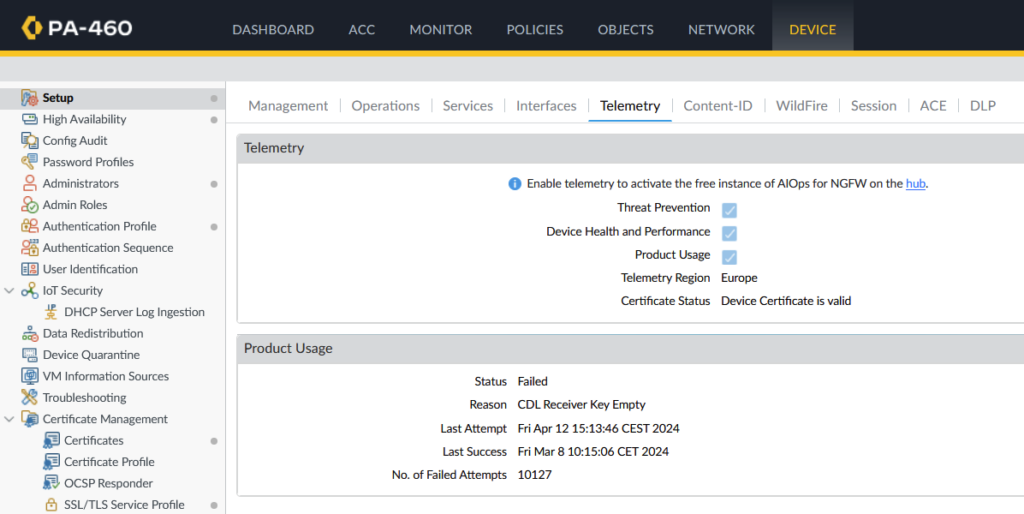
Telemetry configuration
You can verify whether you have device telemetry enabled by checking your firewall web interface (Device > Setup > Telemetry).
Remediation steps
- Temporarily disable device telemetry until the device is upgraded to a fixed PAN-OS version. Once upgraded, device telemetry must be re-enabled on the device. Update 17.4.2024: Disabling device telemetry is no longer an effective mitigation. Please upgrade asap to the recommended hotfixes!
- Enable vulnerability protection to the GlobalProtect interface to prevent exploitation of this issue. Palo Alto Networks has published a threat signature with ID 95187 (introduced in Applications and Threats content version 8833-8682) to block the these attacks. Please see https://live.paloaltonetworks.com/t5/globalprotect-articles/applying-vulnerability-protection-to-globalprotect-interfaces/ta-p/340184 for more information.
More information
The advisory provides more information and guidance. Please forward this information in your respective teams, to make sure everybody who needs to know is aware of this.
![]()

