Motivation
As a distributor we offer various security products from different vendors. On the one hand these are FortiGate and PaloAltoNetworks NGFW firewalls to make the perimeter more secure, on the other hand products & services from Kaspersky. Kaspersky offers various threat feeds that can be used in other products. So why not extend FortiGates and PAN NGFW with these feeds from Kaspersky to increase security even more? Here are my first experiences.
Kaspersky Threat Intelligence Portal
Kaspersky provides the threat feeds through various sources like JSON via HTTPS or STIX via TAXII.
A good starting point is the Kaspersky Threat Intelligence Portal, which provides sample Threat Data Feed, their description and various tools and much more information about threats. The number of available feeds depends on your chosen license.
Kaspersky Threat Intelligence Portal (Login required)
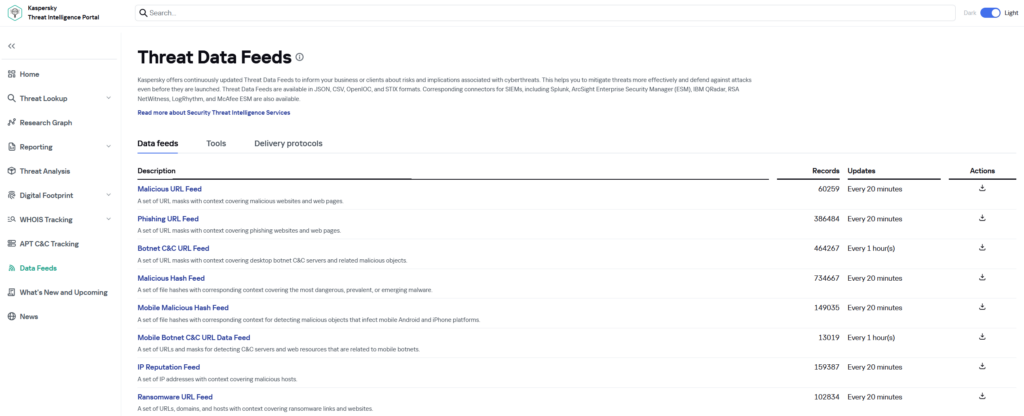
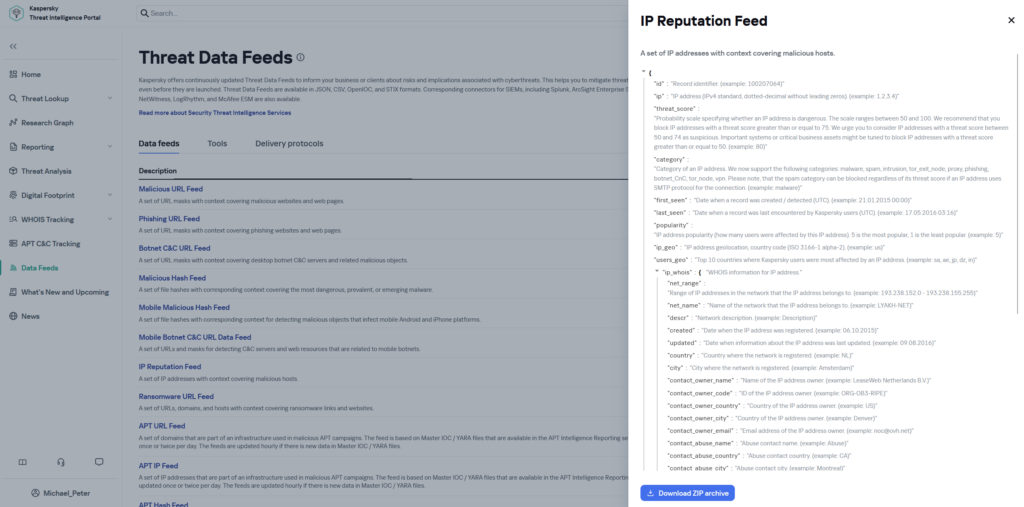
Downloading threat feeds
For further use of the threat feeds, these can be downloaded using two tools provided by Kaspersky, the Kaspersky Data Feed Downloader. and the Kaspersky Feed Utility.
Kaspersky Data Feed Downloader
This Is primarily a Python script to download the Kaspersky Threat Data Feeds from an HTTPS-based service.
Kaspersky Feed Utility
The Kaspersky Feed Utility is a multifunction high-performance tool that allows downloading, converting and filtering Threat Intelligence Data Feeds from Kaspersky according to a specified set of rules. For example, it allows converting Data Feeds (to STIX, OpenIOC, CSV, plain text, PCRE), splitting into multiple files, creating diff files, and much more.
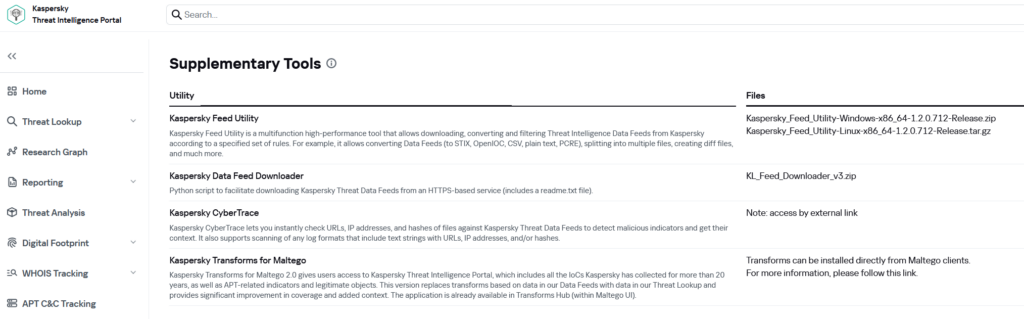
Kaspersky Feed Utility is provided for Window and Linux.
I decided to use the Kaspersky Feed Utility and installed the provided Windows version in my lab.
After installing the tool, different Python scripts are available. I used first a script do display the possible threat lists for download. Kaspersky provides different demo feeds for test purposes which I’m using here:
C:\...\Kaspersky_Feed_Utility\>python demo-kl_feed_downloader.py --list
Id Feed name Usage in downloader
85 TI_Demo_Botnet_C&C_URL_Data_Feed used
86 TI_Demo_Malicious_Hash_Data_Feed used
87 TI_Demo_IP_Reputation_Data_Feed usedFor each feed, you can configure the format and number of fields which should be downloaded. For the firewalls we need plaintext lists that have one entry per line of an IP, a domain or a hash value. Here as example you can see the configuration file for the feed with ID 87, the Demo IP Reputation Feed. The configuration determines the download of the feed as a text file with one IP per line and only entries with a threat score higher than 75.
<?xml version="1.0" encoding="utf-8"?>
<Settings>
[...]
<Feeds>
<OutputFormat delimiter=";" indicatorPerLine="1">txt</OutputFormat>
<Feed enabled="true">
<Name>IP_Reputation_Data_Feed</Name>
<FeedID>87</FeedID>
<FeedFields>category;domains;files/MD5;files/SHA1;files/SHA256;files/threat;first_seen;id;ip;ip_geo;ip_whois/asn;ip_whois/contact_abuse_country;ip_whois/contact_abuse_email;ip_whois/contact_abuse_name;ip_whois/contact_owner_city;ip_whois/contact_owner_code;ip_whois/contact_owner_country;ip_whois/contact_owner_email;ip_whois/contact_owner_name;ip_whois/country;ip_whois/created;ip_whois/descr;ip_whois/net_name;ip_whois/net_range;ip_whois/updated;last_seen;popularity;threat_score;users_geo;</FeedFields>
<Filters>
<Field name="threat_score" value="[75;*]"/>
</Filters>
<RequiredFields>ip</RequiredFields>
</Feed>
</Feeds>
[...]
</Settings>If the configuration is defined, we can download these with a batch file using the Feed Utility (kl_feed_util.exe).
I defined three lists as already mentioned and downloaded these using the utility:
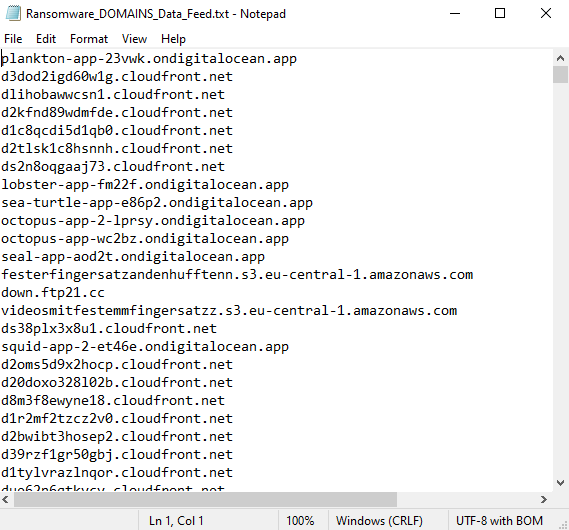
kl_feed_util.exe --config demo_feeds.confAs a result we downloaded three text files. A list with bad reputation IP addresses, one with ransomware domains and one with malicious hash values. As mentioned, these are demo feeds and do not contain real data.
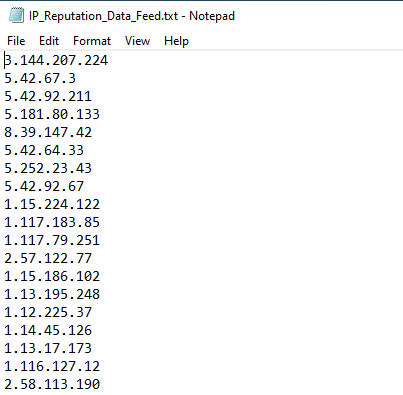
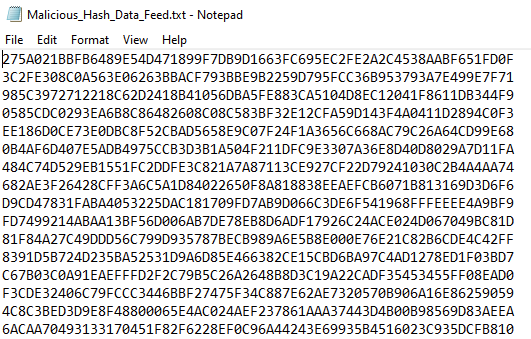
Firewall Integration
FortiGate: Using Security Fabric > External Connectors
With FortiGates, you can use external feeds with the External Connectors feature. You can use feeds containing IP addresses, domain names and malware hashes for use in firewall policies and security profiles.

Palo Alto Networks NGFW: Objects > External Dynamic Lists
Next Generation Firewalls from Palo Alto Networks can integrate threat feeds with the External Dynamic Lists (EDL) feature since a longtime. With the EDL feature you can choose between IP lists, Domain lists or URL lists which can be used in security policies and security profiles.

Here is an example of an EDL fetching the IP Reputation list we downloaded earlier from an internal web server.
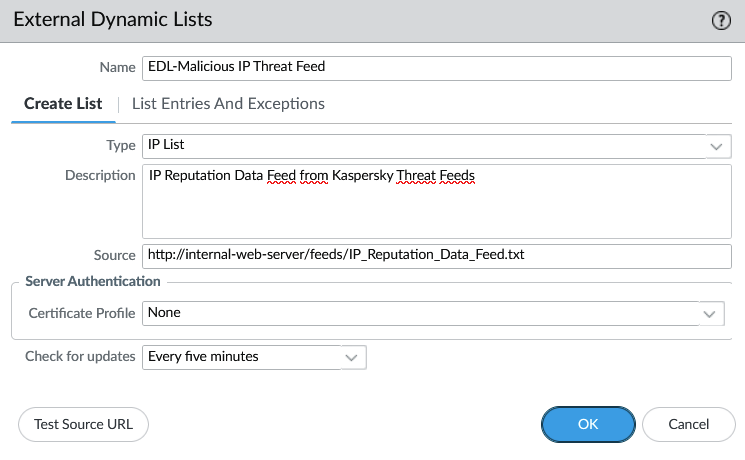
For further details you can check the following blog article where you can find step-by-step instructions how to configure an EDL:
Threat Feed Integration with STIX/TAXII format
Kaspersky also offers their threat feeds in STIX/TAXII format. And FortiGates supports TAXII version 2 format. So instead of downloading and converting the feeds you can directly integrate the feeds via External Connectors on the FortiGate.
STIX format for external threat feeds documentation:
https://docs.fortinet.com/document/fortigate/7.2.6/administration-guide/400345/stix-format-for-external-threat-feeds
First we also need to check which Kaspersky Thread Feeds are available for STIX/TAXII integration. We use a curl command to fetch the collection list for TAXII version 2.1 compatible with FortiGates, redacted because of license regulations.
curl -v -k -H "Accept: application/taxii+json;version=2.1" -u taxii:password https://taxii.tip.kaspersky.com/v2/collections/
[{"id":"76d8*******************************9c32","title":"TAXII_Phishing_URL_Data_Feed","description":"TAXII_Phishing_URL_Data_Feed","can_read":true,"can_write":false,"media_types":["application/stix+json;version=2.1"]},
{"id":"b2d2*******************************46b5","title":"TAXII_Botnet_CnC_URL_Data_Feed_Indicators","description":"TAXII_Botnet_CnC_URL_Data_Feed_Indicators","can_read":true,"can_write":false,"media_types":["application/stix+json;version=2.1"]},
{"id":"8959*******************************d305","title":"TAXII_Mobile_Malicious_Hash_Data_Feed_SHA256","description":"TAXII_Mobile_Malicious_Hash_Data_Feed_SHA256","can_read":true,"can_write":false,"media_types":["application/stix+json;version=2.1"]},
{"id":"0466*******************************3de38","title":"Ransomware_URL_Data_Feed","description":"Ransomware_URL_Data_Feed","can_read":true,"can_write":false,"media_types":["application/stix+json;version=2.1"]},
[and many more ...]You can now select a specific collection and retrieve it directly in the FortiGate External Connector. Here are four examples of available STIX/TAXII feeds, redacted because of license regulations.
TAXII_Phishing_URL_Data_Feed
stix://taxii.tip.kaspersky.com/v2/collections/76d8*******************************9c32/objects/
IP_Reputation_Data_Feed_High_Confidence
stix://taxii.tip.kaspersky.com/v2/collections/b2d2*******************************46b5/objects/
TAXII_Mobile_Malicious_Hash_Data_Feed_SHA256
stix://taxii.tip.kaspersky.com/v2/collections/8959*******************************d305/objects/
Ransomware_URL_Data_Feed
stix://taxii.tip.kaspersky.com/v2/collections/0466*******************************3de38/objects/
And here is the corresponding configuration in the External Connector:
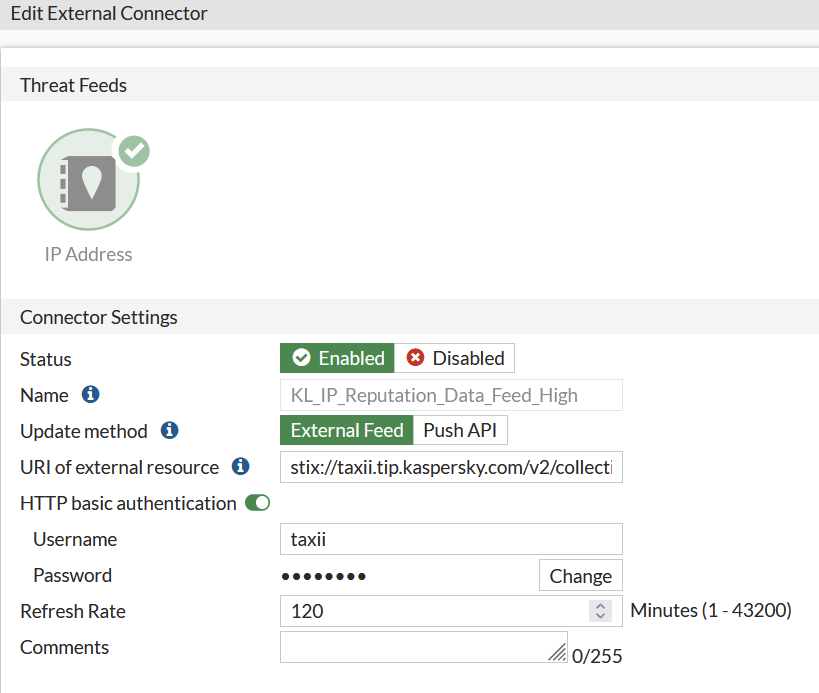
After the first fetch of the list, you can see that the FortiGate has downloaded new entries.
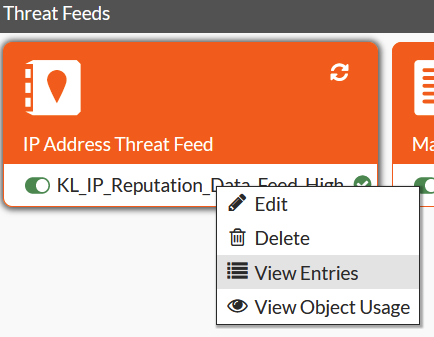
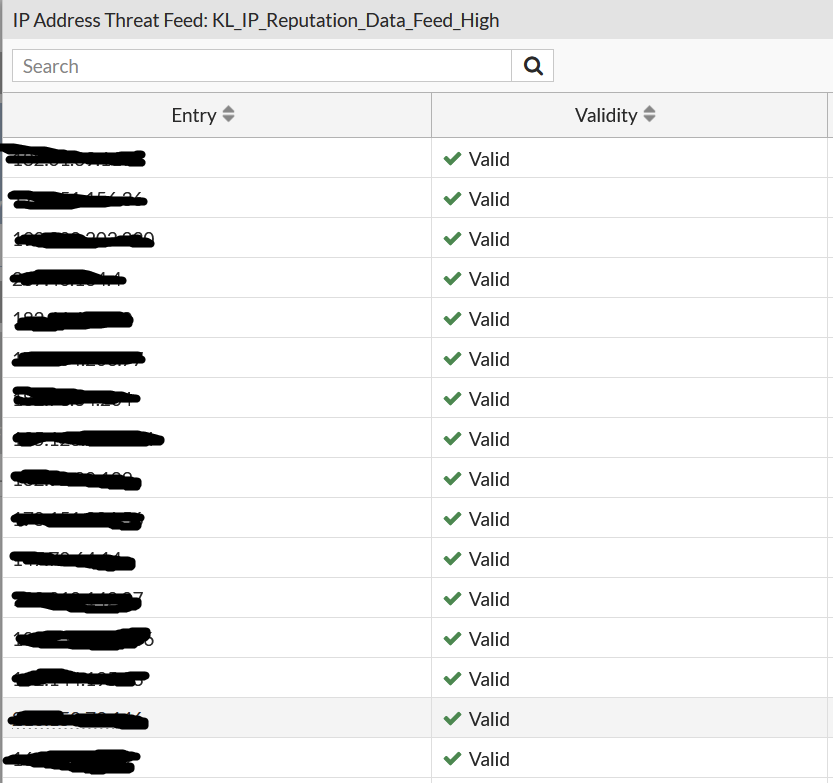
So feel free to integrate different feeds for further usage in firewall policies or security profiles.
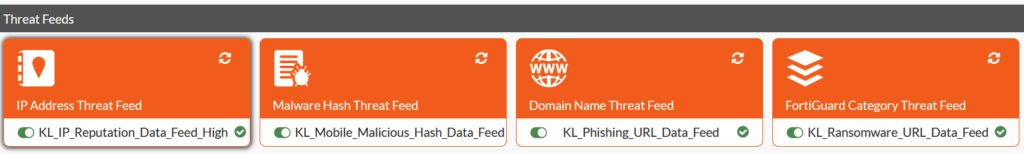
Attention: The use of external connectors can increase the memory consumption of the FortiGate unit. In addition, the number of entries and the disk consumption is limited. According to the latest information, there are 100,000 entries. However, some threat feeds contain more than 100’000 entries. Therefore, it makes more sense to make a preselection with the Feed Utility and download a correct and usable number of entries.
![]()

