German Version: CVE-2022-40684 – Fortinet Authentication bypass on administrative interface (HTTP/HTTPS) (Deutsch)
You have certainly (and hopefully) read the information on the published Fortigate administration access vulnerability and applied the appropriate patches. We have compiled all the information again here for your convenience.
Official CVE information: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-40684
Fortinet PSIRT: https://www.fortiguard.com/psirt/FG-IR-22-377
Fortinet Blog: https://www.fortinet.com/blog/psirt-blogs/update-regarding-cve-2022-40684
Problem
An attacker can gain access to the configuration with a special URL without having to authenticate if the administration access (HTTPS on the WAN interfaces) is open from the outside.
Instructions on how this link should look like are already publicly available. Therefore, a compelling action is necessary!
Affected FortiOS versions
- FortiOS versions 5.x and 6.x are NOT impacted.
- FortiOS version 7.2.0 through 7.2.1
- FortiOS version 7.0.0 through 7.0.6
For other affected products (FortiProxy and FortiSwitchManager) check the PSIRT article.
Workaround for affected releases
Configure local-on policies according to the PSIRT article.
Patches for FortiOS
- For FortiOS 7.0.X –> Install Patch 7.0.7 or 7.0.8
- For FortiOS 7.2.X –> Install Patch 7.2.2
For other affected products (FortiProxy and FortiSwitchManager) check the PSIRT article.
Common best practices
In addition to installing the latest patches, here is a compilation of other security measures that improve the protection of the FortiGate:
- Restrict logins to trusted hosts: https://docs.fortinet.com/document/fortigate/6.4.0/hardening-your-fortigate/582009/system-administrator-best-practices or guide in the PSIRT article.
- Disable administrative access to any external (Internet-facing) interface. Perform administrative tasks over an out-of-band network
- Implement 2FA where possible
- Implement the recommendations in the FortiOS hardening guide: https://docs.fortinet.com/document/fortigate/6.4.0/hardening-your-fortigate/
Am I compromised?
Check your System Logs for the user “Local_Process_Access” and check the Log Description what has been done.
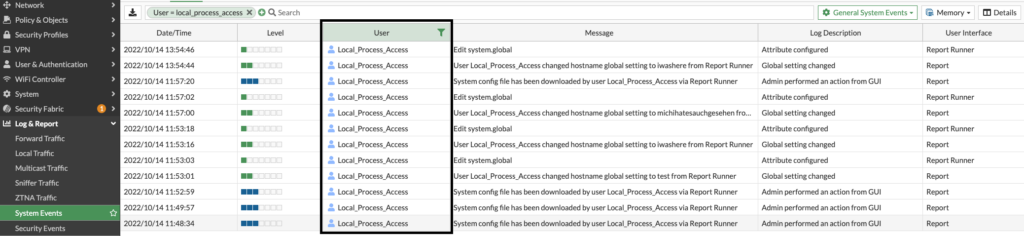
My configuration has been downloaded. Can passwords be read from the configuration?
It depends. If you use a hard-coded cryptographic key to cipher sensitive information, no sensitive information can be used. https://www.fortiguard.com/psirt/FG-IR-19-007
If you’re not using a hardcoded cryptographic key, consider changing all passwords such as admin, user, remote user, IPSEC preshared keys, RADIUS secrets and revoke your certificates. Please refer to the following article:
https://community.fortinet.com/t5/FortiGate/Technical-Tip-Verify-the-private-data-encryption-feature/ta-p/214124
We created an extra blog post for this topic: Remediation steps for FG-IR-22-377 / CVE-2022-40684
![]()

