I recently came across the requirement to connect two vsys on a NGFW appliance. Let’s assume we have two vsys, vsys1 and vsys2. One way is to use a network cable to connect a port in vsys1 to a port in vsys2 in terms of hardware. However, there is another way to connect the two VSYS logically. Let’s dive into the configuration.
vsys configuration
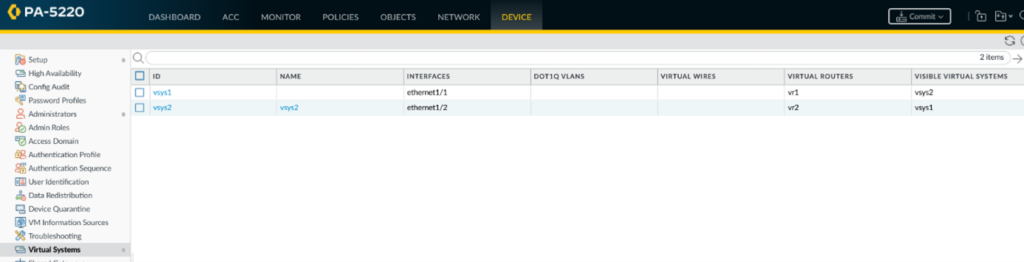
First I configured the two vsys. The “Visible Virtual Systems” option is important here. I specified vsys2 in vsys1 and vsys1 in vsys2 as visible virtual system. This allows me to see the other vsys and use it in the further configuration. This option is required for virtual systems that need to communicate with each other.
Zones
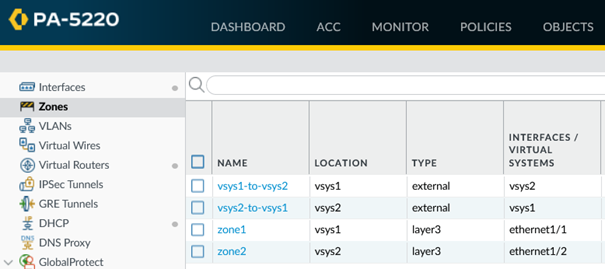
Let’s get to the magic sauce. The communication between vsys1 and vsys2 is achieved by configuring security policies. But as you know, the mandatory configuration is at least a source zone and a destination zone. But how can the zone between the vsys be addressed? The solution here is called “External Zone”.
An external zone is a security object that is associated with a specific virtual system that it can reach. The zone is external to the virtual system. A virtual system can have only one external zone, regardless of how many security zones the virtual system has within it. External zones are required to allow traffic between zones in different virtual systems, without the traffic leaving the firewall.
https://docs.paloaltonetworks.com/pan-os/11-1/pan-os-admin/virtual-systems/communication-between-virtual-systems/inter-vsys-traffic-that-remains-within-the-firewall/external-zone
Let’s take a look at my configuration. I have one internal zone per vsys (zone1 and zone2). And then these external zones (vsys1-to-vsys2 and vsys2-to-vsys1 from type external), each pointing into the other vsys.
Virtual Router
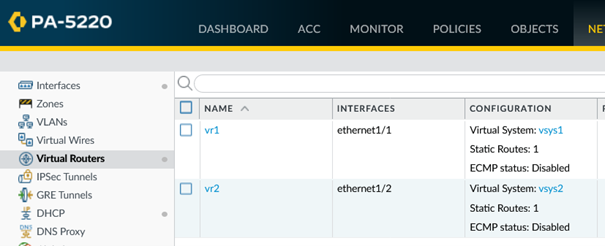
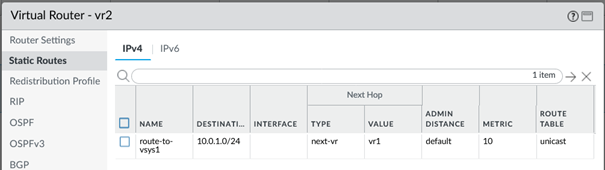
We have connected the two vsys through the external zones. Now each vsys still needs to know which networks are accessible in the other vsys and to whom it must send this traffic. In my case, one route per vsys that points to the other vsys.
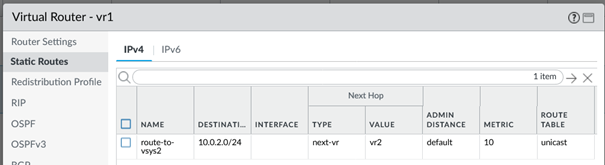
In detail, the route per vsys looks like this. It is important to specify the type “next-vr” and the other vsys in the value field.
Security Policies
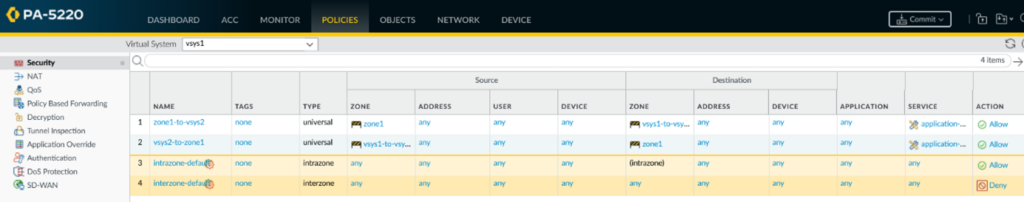
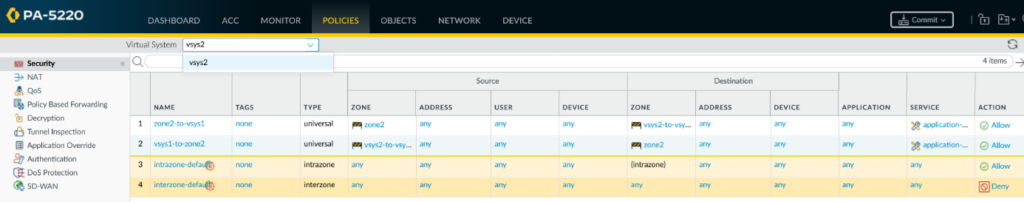
Of course, the security policies are still missing so that traffic between the two vsys is permitted. I have created two policies for each vsys. One from the local zone to the external zone, and one from the external zone to the local zone. And this, as I said, in each vsys to allow traffic in both directions. Of course, only what should be allowed should be added here.
Traffic Monitor
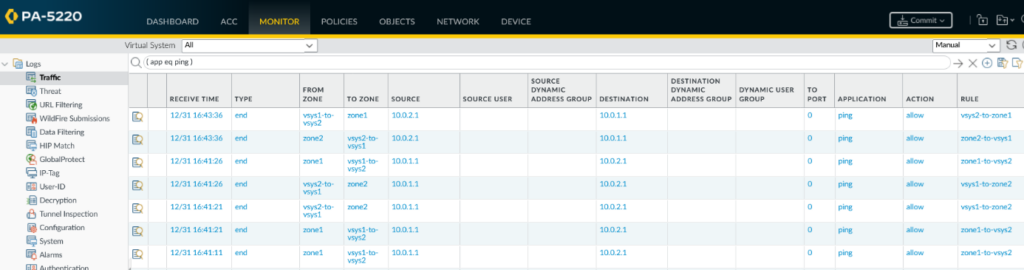
Once the configuration has been carefully created, the two networks should be able to communicate. Of course, this traffic is also logged and can be seen in the traffic log with all the details. You can see exactly which zone the traffic came from and to which zone it was sent. You can also see whether the external zone was used.
Hope that helps. Have fun!
![]()

